Shamoon DistTrack
Overview
Very first attacks had been seen back in 2012 to Saudi Aramco. By the end of the 2016 and start of 2017 more than 15 government agencies and organizations have been hit with Shamoon 2. If one of your employees opened malicious spear phishing document and if you are in Saudi Arabia, you should be aware of DistTrack malware within your network as it is highly destructive.
RecommandationsThe following is guidance for detecting or preventing DistTrack malware within your . Please note that performing any of these actions might have a negative effect on your business and should not be implemented without proper review and study of the impact of the environment
- Monitor for Remote Registry service starts.
- Monitor any events in the SIEM that show dates in between 1 and 20 of August 2012.
- Monitor system time change events back to 2012
- Monitor scheduled jobs and system32 file changes
- Prevent and limit access to SMB shares
- Prevent or throttle client to client communication
- Change credentials of all privileged accounts, make sure that local Administrative passwords are unique
Indicators of Compromise
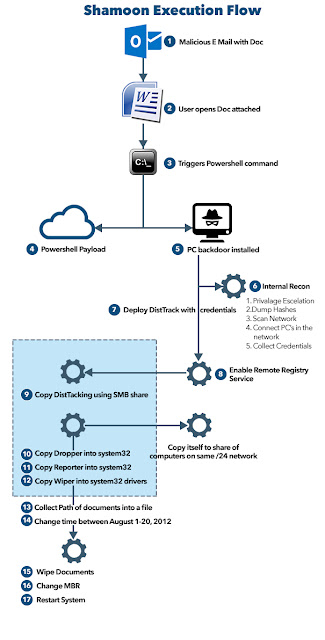
- Attackers send a spear phishing email to employees at the target organization. The email contains a Microsoft Office document as an attachment.
- Opening the attachment from the email triggers PowerShell and enables command line access to the compromised machine.
- Attackers can now communicate with the compromised machine and remotely execute commands on it.
- The attackers escalate privileges and their access to deploy additional tools and malware to other endpoints.
- Attackers study the network by connecting to additional systems and locating critical servers.
- The attackers deploy the Shamoon (DistTrack) malware.
- A coordinated Shamoon (DistTrack) outbreak begins and computer hard drives across the organization are permanently wiped.
When the worm is executed, it copies itself to the following network shares:
\ADMIN$
\C$\\WINDOWS
\D$\\WINDOWS
\E$\\WINDOWS
Dropper
Path: %SYSTEMROOT%\System32File name:
trksvr.exe
ntssrvr32.exe
ntssrvr64.exe
ntssrvr32.bat
gpget.exe
key8854321.pub
Reporter
Path: %SYSTEMROOT%\System32File name: netinit.exe
Wiper
Path: %SYSTEMROOT%\System32File name:
caclsrv, certutl, clean, ctrl, dfrag, dnslookup, dvdquery, event, extract, findfile, fsutl, gpget, iissrv, ipsecure, msinit, ntx, ntdsutl, ntfrsutil, ntnw, power, rdsadmin, regsys, routeman, rrasrv, sacses, sfmsc, sigver, smbinit, wcscript
Driver
The file is digitally signed by “EldoS Corporation"File name: drdisk.sys
Path: %SYSTEMROOT%\System32\Drivers
Affected Platforms
Any Windows installed machine with credentials stolen.
References
https://www.symantec.com/security_response/writeup.jsp?docid=2012-081608-0202-99&tabid=2http://www.2-viruses.com/remove-shamoon-malware
https://securityintelligence.com/the-full-shamoon-how-the-devastating-malware-was-inserted-into-networks/
https://www.fireeye.com/blog/threat-research/2016/11/fireeye_respondsto.html
DETECTION WITH CRYPTOSIM
CSIM-ID: 663426
Title: DistTrack(Shamoon)
Description: Detects DistTrack malware
Author: bilkobe
Reference:
Date: 12.02.2017
Logsource:
Type: firewall
Type: webserver
Product: windows
Service: security
Description: 'Requirements: Audit Policy : Detailed Tracking > Audit Process creation'
Detection:
Timeframe: 120 sn
Keywords:
- 'DistTrack'
- 'Shamoon'
Filter:
Selection1:
# Remote Registery service changed from disabled
# Requires Windows System Logs
EventID: 7040
param4:
- 'RemoteRegistry'
param2:
- 'disabled'
Selection2:
# Requires group policy 'Audit Process Creation'
EventID: 4688
NewProcessName:
- '*\System32\trksvr.exe'
- '*\System32\ntssrvr32.exe'
- '*\System32\ntssrvr64.exe'
- '*\System32\ntssrvr32.bat'
- '*\System32\netinit.exe'
Selection3:
# Requires Windows Security Logs
EventID: 4616
NewTime:
- "2012-08-*
Condition: selection1 or selection2 or Selection3
Tarık KOBALAS
Chief Technology Officer

Yorumlar
Yorum Gönder